Friday, December 31, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -4
This summary is not available. Please
click here to view the post.
Thursday, December 30, 2010
Send Anonymous SMS within India.
SMS servers are quite common these days but it's really difficult to find a completely anonymous sms server. One such site which sends completely anonymous sms is foosms.com. This site is limited to Indian numbers only.
Wednesday, December 29, 2010
WackoPicko : Vulnerable website for Security Evaluation
WackoPicko is a vulnerable web applications to hone your skills or test the latest web vulnerability scanner. It allows to check multiple vulnerabilities which you can test. It was first used for the paper Why Johnny Can't Pentest: An Analysis of Black-box Web Vulnerability Scanners.
Tuesday, December 28, 2010
AddedDomains.com : Must for Startups
 When someone decides for bring up a startup, one of the most important thing one comes across is the domain name. Domain name should be chosen wisely. It shouldn't be a long boring, tough to remember name or short, hard to decipher type. You have to make sure the domain name is available and if there are similarly named sites already. Here is a site that will aid choosing an appropriate domain name.
When someone decides for bring up a startup, one of the most important thing one comes across is the domain name. Domain name should be chosen wisely. It shouldn't be a long boring, tough to remember name or short, hard to decipher type. You have to make sure the domain name is available and if there are similarly named sites already. Here is a site that will aid choosing an appropriate domain name. Saturday, December 25, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -3
This summary is not available. Please
click here to view the post.
Labels:
md5 cracker,
Security Issues,
SQL Injection Attacks
Thursday, December 23, 2010
Google's new feature: Hacked site alert.
Google has added a new feature to it's search engine. It can alert the users in its search result for websites that might have been compromised by displaying the link - 'This site may be compromised'. When users click the new "This site may be compromised" link, they get directed to more information in the Help Center. The websites flagged as compromised are still accessible.
It's a great idea to alert the naive users from being affected by malware & spyware & avoid affecting other users. Google plans to alert the hacked site's webmaster, as well, Wald said. The search engine giant already provides a notification in search results for sites that are potentially serving up malware.
It's a great idea to alert the naive users from being affected by malware & spyware & avoid affecting other users. Google plans to alert the hacked site's webmaster, as well, Wald said. The search engine giant already provides a notification in search results for sites that are potentially serving up malware.
Wednesday, December 22, 2010
CONFICKER Worm : How to remove & protect your systems?
If you are a technical user, you can follow these steps:
http://www.microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=en
Other customers can follow these steps to remove W32/Conficker.worm and prevent it from spreading:
1. Install Microsoft Security Update MS08-067: http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
http://www.microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=en
Other customers can follow these steps to remove W32/Conficker.worm and prevent it from spreading:
1. Install Microsoft Security Update MS08-067: http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Tuesday, December 21, 2010
CONFICKER Worm : What does it can do?
 |
Win32/Conficker.B might spread through file sharing and via removable drives, such as USB drives. It adds a malicious file to the removable drive so that when the drive is used, the AutoPlay dialog box will show one additional option. The Conficker worm can also disable important services on your computer. The option Open folder to view files — Publisher not specified was added by the worm
Monday, December 20, 2010
CONFICKER Worm : What is it anyways?
 Conficker, formally named W32/Conficker.worm, also known as Downup, Downadup and Kido. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has spread rapidly into what is now believed to be the largest computer worm infection since the 2003. Researchers have found 5 variants of conflickers - Conficker.A, Conficker.B, Conficker.C, Conficker.D & Conficker.E.
Conficker, formally named W32/Conficker.worm, also known as Downup, Downadup and Kido. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has spread rapidly into what is now believed to be the largest computer worm infection since the 2003. Researchers have found 5 variants of conflickers - Conficker.A, Conficker.B, Conficker.C, Conficker.D & Conficker.E.Sunday, December 19, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -2
In the previous post, we have seen a basic sql attack structure. In this site, we will understand - how to find sql attack vulnerable site. To find SQL vulnerable sites, we can use google. We search for a specific strings in google to get sites which are revealing some information about the site. Such strings are called 'Google Dorks'. After that, we will check whether the site is vulnerable or not.
Most of these Dorks are found in .php sites.
Most of these Dorks are found in .php sites.
Saturday, December 18, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -1
SQL Injection attacks are one the most well known penetration attacks. Major id theft/credit card/bank theft are conducted through SQL injection attacks. It's easy to implement & if you are well versed with sql syntax. SQL injection attacks are carried on by injecting dangerous SQL queries in the sql database of a site/organisation to make it to fetch sensitive/classified collection of data which may be username & password or email address or credit card no.
Thursday, December 16, 2010
TwitterPasswordDecryptor – Recover Twitter Passwords
TwitterPasswordDecryptor is a free CLI/GUI tool for Windows(XP/Vista/7) to instantly recover Twitter account passwords stored by popular web browsers. Most web browsers store the login credentials for visited websites for users. Each of these web browsers use their own proprietary encryption mechanism to store.
Wednesday, December 15, 2010
SQLInject-Finder: Anti SQL-Injection Tool
SQLInject Finder is an anti sql injection tool. It's a simple python script which parse through the .pcap file looking for suspicious POST & GET sql injects. Rules can also be added to check. Output can be printed on the command line or in tab delimited format.
The output includes:
The output includes:
- The suspicious IP address
- The attacked webpage
- The parameter and value used
- The frame number of the packet within the pcap (can be used to find exactly where the packet is in Wireshark)
- The reason why the request was flagged
Tuesday, December 14, 2010
AmIHackerProof.com 2.0 : Free Vulnerability Scanner Security Service
LIGATT security International launched the upgrade version of their new web service, AmIHackerProof 2.0 for the everyday customers & small business who can't afford to pay large sum of money for security audit. AmIHackerProof 2.0 is an online security audit service with the capability to detect vulnerabilities on a person's computer, or network. The service is free of cost.
Sunday, December 12, 2010
Tool used in DDoS ProWikileaks attack: Operation Payback
Week past we have seen DDoS attack focussed on corporates which denied service to Wikileaks. The number of attackers increased rapidly from double digit to 4 digits. Credit goes to a open source tool which was modified to accomplise the desired results. Tool is java LOIC a Java port of Low Orbit Ion Cannon. The tool was basically designed to test a system imunity to attacks. The tool is exceptionally simple to use. There are just 2 important buttons on it - get orders & fire.
Sunday, December 5, 2010
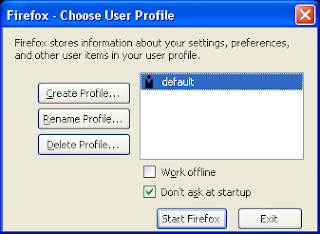
Creating multiple profiles in Mozilla Firefox.
Many folks don't know that they can create different user profiles within a Firefox browser quite similat to creating different users in a OS. Different profile for different persons sharing the same computer is a cool feature respecting the privacy of each users. The process is quite simple:
- Close Firefox, make sure Firefox is not running, check in taskbar.
- Goto start > run
- type 'firefox -p'
- A new dialog box will open up, asking for creating the profile , then follow the instructions.
- You can make the firefox to ask you everytime to use a particular profile, by unchecking the checkbox -Don't ask at startup.
Friday, December 3, 2010
LFIMAP – Scan For Files having LFI (Local File Inclusion) Vulnerablilty
LFI issue has been addressed by some other tools like fimap & inspathx:
fimap is a python tool which can find, prepare, audit, exploit and even google automatically for local and remote file inclusion bugs in webapps. fimap is similar to sqlmap just for LFI/RFI bugs instead of sql injection.
inspathx is a tool that uses local source tree to make requests to the URL and searches for path inclusion (Full Path Disclosure) error messages. It’s a very common problem in PHP web applications that crops up a lot.
A LFIMAP was released recently which focuses purely on LFI attacks.
fimap is a python tool which can find, prepare, audit, exploit and even google automatically for local and remote file inclusion bugs in webapps. fimap is similar to sqlmap just for LFI/RFI bugs instead of sql injection.
inspathx is a tool that uses local source tree to make requests to the URL and searches for path inclusion (Full Path Disclosure) error messages. It’s a very common problem in PHP web applications that crops up a lot.
A LFIMAP was released recently which focuses purely on LFI attacks.
Thursday, December 2, 2010
Defending yourself form firesheep http hijacking
Firesheep makes http hijacking real easy. This type of attack is not new, principle concept had been used many times in previous attacks. Firesheep makes the exploit easier as it is a point & click method, thats where the difference lies. https sites are immune to Firesheep attacks.
Firesheep looks for authentication cookies in open wireless networks & steals them. People using social network sites need to be cautious about their network.
This type of attack can be made by using tools like wireshark but then it requires certain level of expertise.
Firesheep looks for authentication cookies in open wireless networks & steals them. People using social network sites need to be cautious about their network.
This type of attack can be made by using tools like wireshark but then it requires certain level of expertise.
Labels:
firefox addson,
firefox tweak,
firesheep,
https everywhere
Subscribe to:
Comments (Atom)