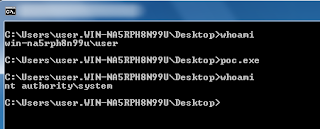
The exploit takes advantage of a bug in win32k.sys, which is part of the Windows kernel. The flaw is related to a registry key which allows an attacker to gain administrative level access. The key has access to almost all windows components & is under full control of the non-administrator users.
The flaw works on XP/vista/7. The bug is not executed through remote code execution. But allows normal users to gain administrative level access.
To prevent the flaw from being exploited you can perform the following actions:
- As an Administrator open Regedit and browse to HKEY_USERS\[SID of each user account]\EUDC
- Right-click EUDC and choose permissions
- Choose the user whose account you are modifying and select Advanced
- Select Add and then type in the user's name and click OK
- Click the Deny checkbox for Delete and Create Subkey
- Click all the OKs and Apply buttons to exit
http://nakedsecurity.sophos.com/2010/11/25/new-windows-zero-day-flaw-bypasses-uac/
http://isc.sans.edu/diary.html?storyid=9988&rss
http://softwareobjects.net/technology/other/bypassing-uac-with-user-privilege-under-windows-vista7/
http://www.exploit-db.com/exploits/15609/
No comments:
Post a Comment