Friday, December 31, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -4
This summary is not available. Please
click here to view the post.
Thursday, December 30, 2010
Send Anonymous SMS within India.
SMS servers are quite common these days but it's really difficult to find a completely anonymous sms server. One such site which sends completely anonymous sms is foosms.com. This site is limited to Indian numbers only.
Wednesday, December 29, 2010
WackoPicko : Vulnerable website for Security Evaluation
WackoPicko is a vulnerable web applications to hone your skills or test the latest web vulnerability scanner. It allows to check multiple vulnerabilities which you can test. It was first used for the paper Why Johnny Can't Pentest: An Analysis of Black-box Web Vulnerability Scanners.
Tuesday, December 28, 2010
AddedDomains.com : Must for Startups
 When someone decides for bring up a startup, one of the most important thing one comes across is the domain name. Domain name should be chosen wisely. It shouldn't be a long boring, tough to remember name or short, hard to decipher type. You have to make sure the domain name is available and if there are similarly named sites already. Here is a site that will aid choosing an appropriate domain name.
When someone decides for bring up a startup, one of the most important thing one comes across is the domain name. Domain name should be chosen wisely. It shouldn't be a long boring, tough to remember name or short, hard to decipher type. You have to make sure the domain name is available and if there are similarly named sites already. Here is a site that will aid choosing an appropriate domain name. Saturday, December 25, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -3
This summary is not available. Please
click here to view the post.
Labels:
md5 cracker,
Security Issues,
SQL Injection Attacks
Thursday, December 23, 2010
Google's new feature: Hacked site alert.
Google has added a new feature to it's search engine. It can alert the users in its search result for websites that might have been compromised by displaying the link - 'This site may be compromised'. When users click the new "This site may be compromised" link, they get directed to more information in the Help Center. The websites flagged as compromised are still accessible.
It's a great idea to alert the naive users from being affected by malware & spyware & avoid affecting other users. Google plans to alert the hacked site's webmaster, as well, Wald said. The search engine giant already provides a notification in search results for sites that are potentially serving up malware.
It's a great idea to alert the naive users from being affected by malware & spyware & avoid affecting other users. Google plans to alert the hacked site's webmaster, as well, Wald said. The search engine giant already provides a notification in search results for sites that are potentially serving up malware.
Wednesday, December 22, 2010
CONFICKER Worm : How to remove & protect your systems?
If you are a technical user, you can follow these steps:
http://www.microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=en
Other customers can follow these steps to remove W32/Conficker.worm and prevent it from spreading:
1. Install Microsoft Security Update MS08-067: http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
http://www.microsoft.com/downloads/details.aspx?FamilyId=AD724AE0-E72D-4F54-9AB3-75B8EB148356&displaylang=en
Other customers can follow these steps to remove W32/Conficker.worm and prevent it from spreading:
1. Install Microsoft Security Update MS08-067: http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Tuesday, December 21, 2010
CONFICKER Worm : What does it can do?
 |
Win32/Conficker.B might spread through file sharing and via removable drives, such as USB drives. It adds a malicious file to the removable drive so that when the drive is used, the AutoPlay dialog box will show one additional option. The Conficker worm can also disable important services on your computer. The option Open folder to view files — Publisher not specified was added by the worm
Monday, December 20, 2010
CONFICKER Worm : What is it anyways?
 Conficker, formally named W32/Conficker.worm, also known as Downup, Downadup and Kido. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has spread rapidly into what is now believed to be the largest computer worm infection since the 2003. Researchers have found 5 variants of conflickers - Conficker.A, Conficker.B, Conficker.C, Conficker.D & Conficker.E.
Conficker, formally named W32/Conficker.worm, also known as Downup, Downadup and Kido. It uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors. Conficker has spread rapidly into what is now believed to be the largest computer worm infection since the 2003. Researchers have found 5 variants of conflickers - Conficker.A, Conficker.B, Conficker.C, Conficker.D & Conficker.E.Sunday, December 19, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -2
In the previous post, we have seen a basic sql attack structure. In this site, we will understand - how to find sql attack vulnerable site. To find SQL vulnerable sites, we can use google. We search for a specific strings in google to get sites which are revealing some information about the site. Such strings are called 'Google Dorks'. After that, we will check whether the site is vulnerable or not.
Most of these Dorks are found in .php sites.
Most of these Dorks are found in .php sites.
Saturday, December 18, 2010
Implementing & Preventing SQL Injection Attacks Tutorial -1
SQL Injection attacks are one the most well known penetration attacks. Major id theft/credit card/bank theft are conducted through SQL injection attacks. It's easy to implement & if you are well versed with sql syntax. SQL injection attacks are carried on by injecting dangerous SQL queries in the sql database of a site/organisation to make it to fetch sensitive/classified collection of data which may be username & password or email address or credit card no.
Thursday, December 16, 2010
TwitterPasswordDecryptor – Recover Twitter Passwords
TwitterPasswordDecryptor is a free CLI/GUI tool for Windows(XP/Vista/7) to instantly recover Twitter account passwords stored by popular web browsers. Most web browsers store the login credentials for visited websites for users. Each of these web browsers use their own proprietary encryption mechanism to store.
Wednesday, December 15, 2010
SQLInject-Finder: Anti SQL-Injection Tool
SQLInject Finder is an anti sql injection tool. It's a simple python script which parse through the .pcap file looking for suspicious POST & GET sql injects. Rules can also be added to check. Output can be printed on the command line or in tab delimited format.
The output includes:
The output includes:
- The suspicious IP address
- The attacked webpage
- The parameter and value used
- The frame number of the packet within the pcap (can be used to find exactly where the packet is in Wireshark)
- The reason why the request was flagged
Tuesday, December 14, 2010
AmIHackerProof.com 2.0 : Free Vulnerability Scanner Security Service
LIGATT security International launched the upgrade version of their new web service, AmIHackerProof 2.0 for the everyday customers & small business who can't afford to pay large sum of money for security audit. AmIHackerProof 2.0 is an online security audit service with the capability to detect vulnerabilities on a person's computer, or network. The service is free of cost.
Sunday, December 12, 2010
Tool used in DDoS ProWikileaks attack: Operation Payback
Week past we have seen DDoS attack focussed on corporates which denied service to Wikileaks. The number of attackers increased rapidly from double digit to 4 digits. Credit goes to a open source tool which was modified to accomplise the desired results. Tool is java LOIC a Java port of Low Orbit Ion Cannon. The tool was basically designed to test a system imunity to attacks. The tool is exceptionally simple to use. There are just 2 important buttons on it - get orders & fire.
Sunday, December 5, 2010
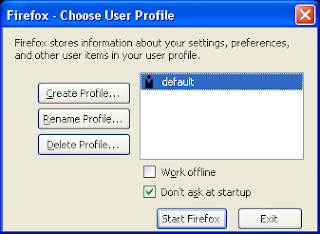
Creating multiple profiles in Mozilla Firefox.
Many folks don't know that they can create different user profiles within a Firefox browser quite similat to creating different users in a OS. Different profile for different persons sharing the same computer is a cool feature respecting the privacy of each users. The process is quite simple:
- Close Firefox, make sure Firefox is not running, check in taskbar.
- Goto start > run
- type 'firefox -p'
- A new dialog box will open up, asking for creating the profile , then follow the instructions.
- You can make the firefox to ask you everytime to use a particular profile, by unchecking the checkbox -Don't ask at startup.
Friday, December 3, 2010
LFIMAP – Scan For Files having LFI (Local File Inclusion) Vulnerablilty
LFI issue has been addressed by some other tools like fimap & inspathx:
fimap is a python tool which can find, prepare, audit, exploit and even google automatically for local and remote file inclusion bugs in webapps. fimap is similar to sqlmap just for LFI/RFI bugs instead of sql injection.
inspathx is a tool that uses local source tree to make requests to the URL and searches for path inclusion (Full Path Disclosure) error messages. It’s a very common problem in PHP web applications that crops up a lot.
A LFIMAP was released recently which focuses purely on LFI attacks.
fimap is a python tool which can find, prepare, audit, exploit and even google automatically for local and remote file inclusion bugs in webapps. fimap is similar to sqlmap just for LFI/RFI bugs instead of sql injection.
inspathx is a tool that uses local source tree to make requests to the URL and searches for path inclusion (Full Path Disclosure) error messages. It’s a very common problem in PHP web applications that crops up a lot.
A LFIMAP was released recently which focuses purely on LFI attacks.
Thursday, December 2, 2010
Defending yourself form firesheep http hijacking
Firesheep makes http hijacking real easy. This type of attack is not new, principle concept had been used many times in previous attacks. Firesheep makes the exploit easier as it is a point & click method, thats where the difference lies. https sites are immune to Firesheep attacks.
Firesheep looks for authentication cookies in open wireless networks & steals them. People using social network sites need to be cautious about their network.
This type of attack can be made by using tools like wireshark but then it requires certain level of expertise.
Firesheep looks for authentication cookies in open wireless networks & steals them. People using social network sites need to be cautious about their network.
This type of attack can be made by using tools like wireshark but then it requires certain level of expertise.
Labels:
firefox addson,
firefox tweak,
firesheep,
https everywhere
Monday, November 29, 2010
Crunch – Password Cracking Wordlist Generator
Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
Download link.
Features
* Crunch generates wordlists in both combination and permutation ways
* It can breakup output by number of lines or file size
* Now has resume support
* Pattern now supports number and symbols
* Pattern now supports upper and lower case characters separately
* Adds a status report when generating multiple files
Download link.
Features
* Crunch generates wordlists in both combination and permutation ways
* It can breakup output by number of lines or file size
* Now has resume support
* Pattern now supports number and symbols
* Pattern now supports upper and lower case characters separately
* Adds a status report when generating multiple files
Friday, November 26, 2010
Pentbox - cool ruby tool for pentesting
Pentbox is a Security Tool Suite that packs security and stability testing oriented tools for networks and systems. It is programmed in Ruby and oriented to GNU/Linux systems, but compatible with Windows, MacOS and every systems where Ruby works. It is free, licensed under GNU/GPLv3. It can be used for port scanning, hash password cracker, implementing dos attack.
These are the tools covered in Pentbox:-
- Cryptography tools
Base64 Encoder & Decoder
Multi-Digest (MD5, SHA1, SHA256, SHA384, SHA512, RIPEMD-160)
Hash Password Cracker (MD5, SHA1, SHA256, SHA384, SHA512, RIPEMD-160)
Secure Password Generator
These are the tools covered in Pentbox:-
- Cryptography tools
Base64 Encoder & Decoder
Multi-Digest (MD5, SHA1, SHA256, SHA384, SHA512, RIPEMD-160)
Hash Password Cracker (MD5, SHA1, SHA256, SHA384, SHA512, RIPEMD-160)
Secure Password Generator
Thursday, November 25, 2010
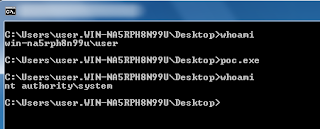
New Windows (working in XP/Vista/7) zero-day flaw bypasses UAC [privilege escalation exploit]
A new privilege escalation exploit has been unraveled. To execute the attack, just download a file & execute the file poc.exe. Your non-administrator user account will be promoted to administrator. See the picture.
Wednesday, November 24, 2010
Sites providing anonymous email services!
Anonymous email sites are a matter of controversy today. Some people take it as medium of treachery whereas others treat it as a useful utility.
The ethical point in using anonymous email sites is you can re-frame from the use of email sites in a public pc where there is a risk email/ password theft.
Here are some anonymous email sites, try them & discover what they are capable of.
http://www.anonymailer.net/ ->Is one of the most trusted anonymous email service that send anonymous email every day over hundreds of free anonymous emails are sent from this website, You can use whatever e-mail address you like as a reply address of from address.Do not require registration.
The ethical point in using anonymous email sites is you can re-frame from the use of email sites in a public pc where there is a risk email/ password theft.
Here are some anonymous email sites, try them & discover what they are capable of.
http://www.anonymailer.net/ ->Is one of the most trusted anonymous email service that send anonymous email every day over hundreds of free anonymous emails are sent from this website, You can use whatever e-mail address you like as a reply address of from address.Do not require registration.
Sunday, November 21, 2010
SHODAN - Vulnerability Scanner search engine.
SHODAN is a search engine that can be used as a vulnerability scanner. It finds specific computers (routers, servers, etc.) using a variety of filters. Some have also described it as a public port scan directory or a search engine of banners.
Open Source Digital Forensics tools collection.
This site initially started by Brian Carrier is now maintained by a team of volunteers, contains a large repository of open source digital forensics tools, papers, images and procedures on digital forensics. If your favourite open source tool is not listed on this site, you can submit it to get added to the list.
Saturday, November 20, 2010
Katana Tool Kit: Portable Applications
The Katana Tool Kit is the ultimate toolkit as it comes preconfigured with over a hundred portable applications.Install it any flash drive (>4Gb) and you can try your hands on many utility/security software. Portable applications are those which do not require installation on a system to be executed. They can be run directly from an external device allowing you to bring all your favorite applications around with you on one drive.
Learn Ruby & Rail through browser!
 Learn Ruby in a user friendly environment through the TryRuby site which provides browser based interface for Ruby learners. No programming experience is required. Rails for Zombies is a series of browser based Ruby on Rails tutorials for beginners that assumes some knowledge of Ruby. This is a quick way to get started learning either Ruby or Ruby on Rails.
Learn Ruby in a user friendly environment through the TryRuby site which provides browser based interface for Ruby learners. No programming experience is required. Rails for Zombies is a series of browser based Ruby on Rails tutorials for beginners that assumes some knowledge of Ruby. This is a quick way to get started learning either Ruby or Ruby on Rails.Thursday, November 18, 2010
Application Layer DDoS Simulator - ddosim v0.2
ddosim is a tool to simulate a distributed denial of service (DDOS) attack against a target server. The objective is to analyze the immunity of the server to handle application specific DDOS attacks. It simulates several zombie hosts (having random IP addresses) which create full TCP connections to the target server. After completing the connection, ddosim starts the conversation with the listening application (e.g. HTTP server).
Wednesday, November 17, 2010
XSSer v1.0 – Cross Site Scripter Framework!
XSSer is another arsenal in your open source penetration testing tool set. It automates the process of detecting and exploiting XSS injections against different applications. It contains several options to try to bypass certain filters, and various special techniques of code injection.
It created for Ubuntu/Debian based systems. XSSer package for Archlinux can be found in the AUR. More info here
It created for Ubuntu/Debian based systems. XSSer package for Archlinux can be found in the AUR. More info here
Tuesday, November 16, 2010
Stuxnet - The standard malware, if not unusually sophisticated!
Symantec has issued a dossier on Stuxnet depicting ins-outs of the malware, who were the targets & what was the objective.
According to Symantec, Stuxnet targets specific frequency converter drives ( only frequency drives from two companies that are running at high speeds – between 807Hz and 1210Hz.) — power supplies that are used to control the speed of a device, such as a motor. The malware intercepts commands sent to the drives from the Siemens SCADA software, and replaces them with malicious commands to control the speed of a device, varying it wildly, but intermittently.
According to Symantec, Stuxnet targets specific frequency converter drives ( only frequency drives from two companies that are running at high speeds – between 807Hz and 1210Hz.) — power supplies that are used to control the speed of a device, such as a motor. The malware intercepts commands sent to the drives from the Siemens SCADA software, and replaces them with malicious commands to control the speed of a device, varying it wildly, but intermittently.
Monday, November 15, 2010
Mozilla Firefox 3.6.12 Remote Denial Of Service - Dated 2010-11-12
 New vulnerability has been exposed in the updated version of the Mozilla Firefox browser by the people behind BackTrack Live pentesting operating system. This OS is most preferred among security professionals.
New vulnerability has been exposed in the updated version of the Mozilla Firefox browser by the people behind BackTrack Live pentesting operating system. This OS is most preferred among security professionals. Sunday, November 14, 2010
FIRESHEEP - new cookie sniffing hack!
Firefox users now have a new & easier point & click tool to sniff others cookies. It's somewhat easier to implement than sidejacking. Firesheep created a frenzy in social network & email users communities some days ago.
Friday, November 12, 2010
Bugmenot.com -- Bypass registration!
While surfing the net, the inevitable process of registration & the confirming the email might render you bored & jaded. Here is an easy way to avoid it. Enter the url -> http://www.bugmenot.com/ & search the site for used logins for the site you want to surf.
Sending SMS to a mobile no. at a scheduled time (only for India)!
In case you want to send a SMS to a person at a given time (in India) than try this site http://sms7.in. The service is particularly useful when you may be busy at the point of time you want to send the SMS to recipient. Like in case you want to send a "Happy Birthday!" message to a friend at 12'oclock at night but you decided to sleep before 12. At such cases, this site comes at your rescue.
Access internet through email!
At times when your internet connection is slow or you have access to email & no access to the internet from ISP. Still you can access web sites through your email.
The http://www.web2pdfconvert.com/ comes handy. It's a useful site which converts your requested page to pdf & mails back.
So to use the service simple send a mail to submit@web2pdfconvert.com with the body
. The site will send you back the pdf of the page within minutes.
The http://www.web2pdfconvert.com/ comes handy. It's a useful site which converts your requested page to pdf & mails back.
So to use the service simple send a mail to submit@web2pdfconvert.com with the body
. The site will send you back the pdf of the page within minutes.
Saturday, October 30, 2010
USBsploit 0.3b : USB Backdoor Generator
USBsploit 0.3b is a proof of concept to generate backdoors & transferring files remotely using autorun files.
It can perform these tasks:
It can perform these tasks:
- generate reverse TCP backdoors
- running Autorun or LNK USB infections
- dumping all USB files remotely on multiple targets at the same time.
Friday, October 29, 2010
Damn Vulnerable Web App : Learn & Test Web Security.
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be light weight, easy to use and full of vulnerabilities to exploit, aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
Sunday, October 10, 2010
Microsoft SQL Server Fingerprinting Tools
SQL Server fingerprinting is an essential step before performing any kind of penetration testing on database servers. There are two well known tools for Microsoft SQL Server Fingerprinting.
SQLPing 3.0 performs both active and passive scans of your network in order to identify all of the SQL Server/MSDE installations in your enterprise. Due to the proliferation of personal firewalls, inconsistent network library configurations, and multiple-instance support, SQL Server installations are becoming increasingly difficult to discover, assess, and maintain. SQLPing 3.0 is designed to remedy this problem by combining all known means of SQL Server/MSDE discovery into a single tool which can be used to ferret-out servers you never knew existed on your network so you can properly secure them. .NET Framework v2.0 Required.
SQLVer has been built to utilise the same techniques as SQLPing.NET 1.3 beta, however, does not actually use a UDP packet sent to port 1434 packet to enumerate the MS SQL server version info. This tool in fact uses TCP port 1433 instead.
ESF is a modern tool, it help identifying granular level findings to further exploit database. ESF works for these versions:
The strengths of Exploit Next Generation SQL Fingerprint are:
SQLPing 3.0 performs both active and passive scans of your network in order to identify all of the SQL Server/MSDE installations in your enterprise. Due to the proliferation of personal firewalls, inconsistent network library configurations, and multiple-instance support, SQL Server installations are becoming increasingly difficult to discover, assess, and maintain. SQLPing 3.0 is designed to remedy this problem by combining all known means of SQL Server/MSDE discovery into a single tool which can be used to ferret-out servers you never knew existed on your network so you can properly secure them. .NET Framework v2.0 Required.
SQLVer has been built to utilise the same techniques as SQLPing.NET 1.3 beta, however, does not actually use a UDP packet sent to port 1434 packet to enumerate the MS SQL server version info. This tool in fact uses TCP port 1433 instead.
ESF is a modern tool, it help identifying granular level findings to further exploit database. ESF works for these versions:
- Microsoft SQL Server 2000
- Microsoft SQL Server 2005
- Microsoft SQL Server 2008
The strengths of Exploit Next Generation SQL Fingerprint are:
- uses both TCP and UDP protocols
- capable to identify multiple Microsoft SQL Server instances and their TCP communication ports.
- does not require any authentication method to identify the Microsoft SQL Server version.
- uses probabilistic algorithm to identify the Microsoft SQL Server version, combining both TCP and UDP fingerprint.
Friday, August 27, 2010
BAT to EXE converter!
Executing a bat file may raise alarm when executed in a victims system. In order to have a stealth execution when can convert the bat or cmd file into exe file. which will execute like any other software. Convert bat to exe file by using Advanced Bat To Exe converter which works on all Windows version including Windows 7.
Saturday, June 19, 2010
Hide your files in jpeg File without any Software!
This is quite an old trick but still works fine. Its a type of stenography technique where we try to hide a file inside another file.
You will only need to download WinRAR & install it.
You will only need to download WinRAR & install it.
Friday, April 30, 2010
Super Hiding the folder easily using cmd command!
For hiding your folder execute the command
X:\> attrib +a +r +s +h foldername /s /d [enter]
For unhiding:
X:\> attrib -a -r -s -h foldername /s /d [enter]
X= x is location for our folder in hard disk.
X:\> attrib +a +r +s +h foldername /s /d [enter]
For unhiding:
X:\> attrib -a -r -s -h foldername /s /d [enter]
X= x is location for our folder in hard disk.
Monday, April 19, 2010
Enabling telnet in vista/7 & Sending anonymous emails!
In Windows Vista & windows7 telnet is disabled by default because of its security issues (passes messages in plain text, easy to sniff passwords & credentials, so its obsolete now).
In order to enable go to control panel
> Programs
> Programs & Features
> click on 'Turn Windows Feature on or off' on the left panel
> new window appears, tick check boxes telnet server or telnet client or both as per your need.
> click ok
> open cmd & start telneting to another telnet enabled computers (for command
queries type telnet /? in cmd)
In order to enable go to control panel
> Programs
> Programs & Features
> click on 'Turn Windows Feature on or off' on the left panel
> new window appears, tick check boxes telnet server or telnet client or both as per your need.
> click ok
> open cmd & start telneting to another telnet enabled computers (for command
queries type telnet /? in cmd)
Monday, April 12, 2010
Creating Linux environment & installing Linux softwares in Windows!
There are plenty of solutions for achieving linux environment in Windows.
1)Installing Cygwin creates linux environment. But all programs are not supported by cygwin. Also it may create problems in newer versions of windows. It consists of two parts:
# A DLL (cygwin1.dll) which acts as a Linux API emulation layer providing substantial Linux API functionality.
# A collection of tools which provide Linux look and feel.
Problems regarding cygwin
# Cygwin is not a way to run native linux apps on Windows. You have to rebuild your application from source if you want it to run on Windows.
# Cygwin is not a way to magically make native Windows apps aware of UNIX functionality, like signals, ptys, etc. Again, you need to build your apps from source if you want to take advantage of Cygwin functionality
1)Installing Cygwin creates linux environment. But all programs are not supported by cygwin. Also it may create problems in newer versions of windows. It consists of two parts:
# A DLL (cygwin1.dll) which acts as a Linux API emulation layer providing substantial Linux API functionality.
# A collection of tools which provide Linux look and feel.
Problems regarding cygwin
# Cygwin is not a way to run native linux apps on Windows. You have to rebuild your application from source if you want it to run on Windows.
# Cygwin is not a way to magically make native Windows apps aware of UNIX functionality, like signals, ptys, etc. Again, you need to build your apps from source if you want to take advantage of Cygwin functionality
Friday, April 2, 2010
Sidejacking -- Serious threat to Wireless Network users!
The purpose of this post is to create awareness about the sense of insecurity while accessing wireless networks & not to encourage illegal hacking activites.
Sidejacking tool is available here. -- http://erratasec.blogspot.com/2007/08/sidejacking-with-hamster_05.html
Sidejacking tool consists of ferret & hamster. Ferret sniffs cookies & hamster convert that cookie information into something Browser can understand, also it acts as internal proxy server. So its a point & click attack & very easy to implement.
Information about sidejacking---
http://www.tgdaily.com/security-features/34324-tg-video-wirelessly-hacking-gmail-and-more-tutorial
http://erratasec.blogspot.com/2008/01/more-sidejacking.html
Sidejacking tool is available here. -- http://erratasec.blogspot.com/2007/08/sidejacking-with-hamster_05.html
Sidejacking tool consists of ferret & hamster. Ferret sniffs cookies & hamster convert that cookie information into something Browser can understand, also it acts as internal proxy server. So its a point & click attack & very easy to implement.
Information about sidejacking---
http://www.tgdaily.com/security-features/34324-tg-video-wirelessly-hacking-gmail-and-more-tutorial
http://erratasec.blogspot.com/2008/01/more-sidejacking.html
Friday, March 19, 2010
Try creating some easy animation!
For creating animations in very easy way, plenty of softwares are available, some are online & some you can download one your pc & use it. I have come across such a software called UnFreez. The resulted animated gif image just takes a collection of gif images & play them with some delay. Its very easy to use.
This is a video from Tinkernut which guides on the usage of UnFreez.
This is a video from Tinkernut which guides on the usage of UnFreez.
Sunday, March 14, 2010
Access (GodMode)Master Control panel in Windows7
Access (GodMode)Master Control panel in Windows7
GodMode is the master Control panel for windows7 which gives access to all control programs. I don't know why they call it GodMode.
Create a new folder in any directory & then rename it through cmd, issue the command.
> ren "New Folder" GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
OR simply
> mkdir GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
GodMode is the master Control panel for windows7 which gives access to all control programs. I don't know why they call it GodMode.
Create a new folder in any directory & then rename it through cmd, issue the command.
> ren "New Folder" GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
OR simply
> mkdir GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
Thursday, March 11, 2010
Firefox inside firefox
This sounds humbug & silly but still you can try this, hope you can use this trick in some innovative way.
write in the url bar -> chrome://browser/content/browser.xul
Firefox inside firefox! (8-D] Enjoy!
write in the url bar -> chrome://browser/content/browser.xul
Firefox inside firefox! (8-D] Enjoy!
Broadcast a video file from your webcam
You may have wondered sometimes that how a video can be broadcasted through a webcam. Here is the solution - Download a webcam software called SuperWebcam http://www.superwebcam.com/download.php . After installing, open the application. You will see the video option menu in the top menu items. Click it & select video file thats all. Now the video file you selected starts on the display of superwebcam display. After that open the yahoo webcam & you will see the same video playing in it too.
Subscribe to:
Posts (Atom)